5 Steps Transfer

Understanding the Process of Transfer

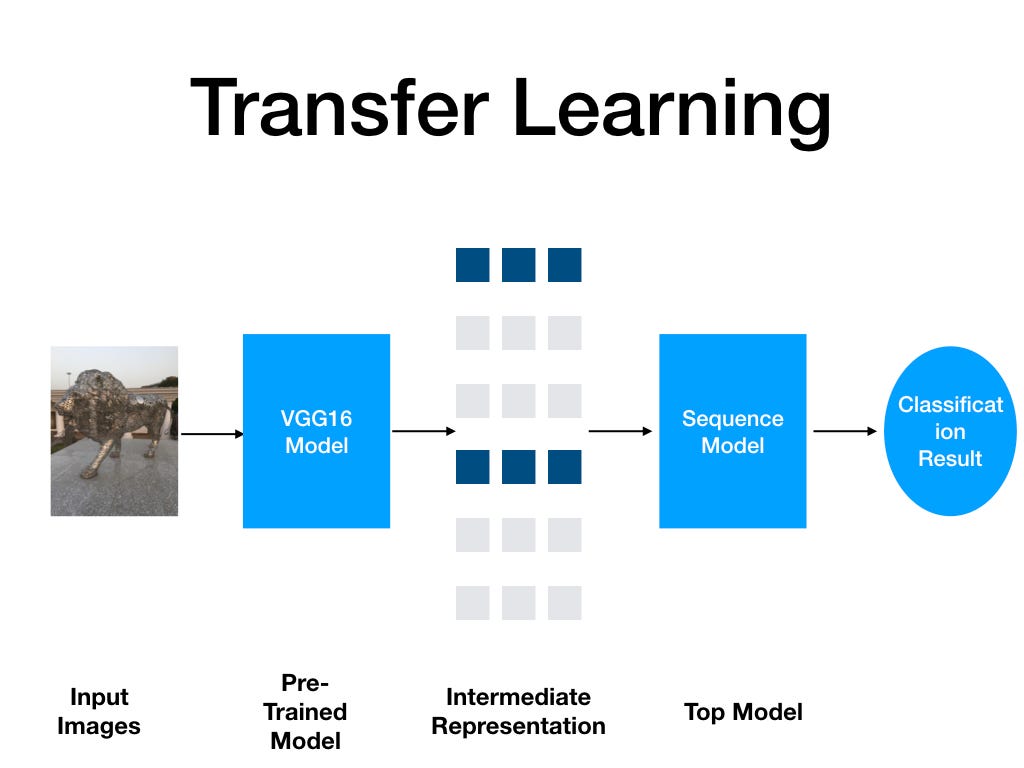
The process of transfer, whether it’s transferring files, data, or even knowledge, involves a series of steps designed to ensure that the transfer is smooth, efficient, and accurate. In the digital age, understanding these steps is crucial for anyone looking to share information or move data from one location to another. This process can be broadly categorized into five key steps, each playing a vital role in the successful completion of a transfer.
Step 1: Preparation

The first step in any transfer process is preparation. This involves identifying the source and the destination of the transfer. Whether you’re transferring files from one computer to another or moving data from an old phone to a new one, knowing exactly what you’re transferring and where it’s going is essential. Preparation also includes checking for compatibility issues and ensuring that both the source and destination devices or systems are fully functional and ready for the transfer. This step is critical in preventing errors and ensuring that the transfer process goes smoothly.
Step 2: Connection Establishment

After preparation, the next step is establishing a connection between the source and the destination. This could involve physically connecting devices via cables, setting up a wireless connection, or configuring network settings to enable data transfer over the internet. The method of connection will depend on the type of transfer being undertaken and the devices or systems involved. Security is also a key consideration at this stage, with measures such as encryption and password protection being used to safeguard the data being transferred.
Step 3: Data Selection and Transfer Initiation
With the connection established, the next step is to select the data to be transferred and initiate the transfer process. This involves choosing the files or data that need to be moved and using the appropriate software or tool to start the transfer. For example, if transferring files between computers, you might use a file transfer protocol (FTP) client or a cloud storage service. The initiation of the transfer process should also include monitoring for any errors or issues that might arise during the transfer, allowing for quick intervention if problems occur.
Step 4: Transfer Execution and Monitoring
The actual transfer of data is the fourth step in the process. This step involves the physical or digital movement of the selected data from the source to the destination. Monitoring the transfer as it happens is crucial, as it allows for the identification of any issues that might arise, such as data corruption, transfer errors, or connectivity problems. Tools and software used for the transfer often provide real-time feedback on the progress of the transfer, including the amount of data transferred, the speed of the transfer, and an estimate of how much longer the transfer will take.
Step 5: Verification and Completion

The final step in the transfer process is verification and completion. Once the transfer is complete, it’s essential to verify that the data has been successfully transferred and is intact and functional at the destination. This involves checking for data integrity, ensuring that no data was lost or corrupted during the transfer, and confirming that the transferred data is accessible and usable. Upon successful verification, the transfer process is complete, and the data is ready for use at its new location.
📝 Note: Always ensure that you have the necessary permissions and follow any applicable laws and regulations when transferring data, especially sensitive or personal information.
In summary, the process of transfer, whether digital or physical, involves a careful series of steps from preparation through to verification and completion. Understanding and following these steps can help ensure that transfers are completed efficiently, securely, and accurately, which is crucial in today’s data-driven world.
What is the most secure method of transferring sensitive data?

+
The most secure method often involves using encrypted connections and secure protocols, such as SFTP or HTTPS, to protect the data during transfer.
How can I ensure the integrity of my data during a transfer?

+
Verifying the integrity of your data involves checking for any corruption or loss during the transfer. This can be done by comparing checksums of the data before and after the transfer or by using tools that provide data integrity checks.
What are some common issues encountered during data transfer?
+
Common issues include connectivity problems, data corruption, transfer errors due to incompatible file systems or formats, and security breaches if proper precautions are not taken.



